The New Threat Landscape: Deconstructing AI-Native Data Risk
AI doesn’t just add risk—it changes where and how data moves. To secure modern workflows, we need to see risks that legacy tools can’t.
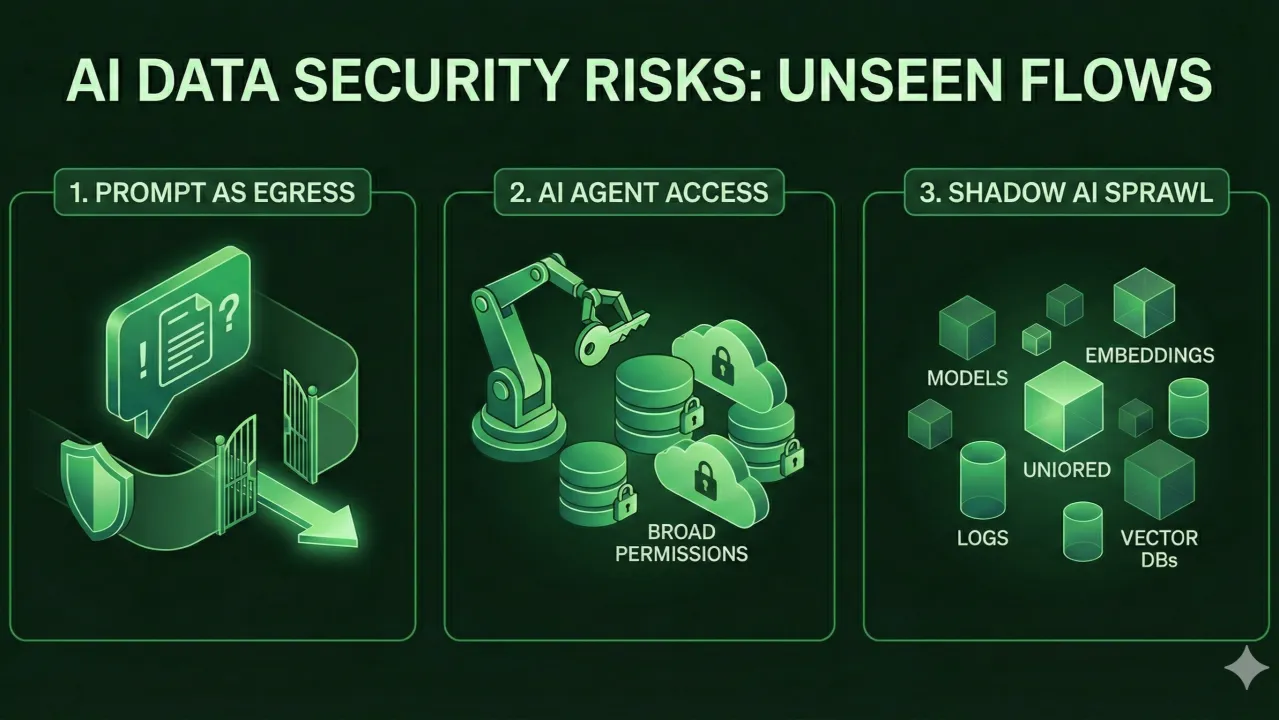
The prompt is the new perimeter
Copilots and assistants are now major egress paths. A harmless request—“summarize this doc”—can place a confidential file into a context window you don’t control. Data exits as conversation, not as a file transfer. Classic, file-centric controls miss it.
Non-human insider risk
AI agents (and service accounts) act with broad, continuous access—drafting emails, sharing code, touching data lakes/SharePoint/CRM. Treat them as first-class identities: separate creds, least privilege, scoped retrieval, full audit. The next breach may come from an over-permissioned agent, not a user.
Sprawl & Shadow AI
Beyond SaaS sprawl, we now have models, embeddings, vector DBs, fine-tunes, prompt/output logs—often outside traditional inventories. New sensitive data emerges (training sets, synthetic data, internal knowledge). DLP tuned for file patterns can’t see prompts, hidden states, or generated outputs.
Bottom Line
AI creates new risk surfaces—prompts, agents, and hidden AI states—but it also provides the blueprint to mitigate them (semantic detection, lineage, AI-edge controls, etc.).
Part 3: The AI-Powered Defense: Reimagining Data Loss Prevention, is on the way…